Secure Everything You Build and Run in the Cloud
Use the Wiz Cloud Security Platform to build faster in the cloud, enabling security, dev and devops to work together in a self-service model built for the scale and speed of your cloud development.
Get a demoTrusted by more than 40% of Fortune 100 companies






The switch to cloud
creates a new world
of security challenges
A new set of problems
requires a new set of solutions
Wiz Cloud
Security Platform


One Cloud Security Command Center For Full Control
DSPM
Continuously monitor for sensitive data and secrets exposure and proactively eliminate attack paths to prevent data breaches.
Learn moreCSPM
Continuously detect and remediate misconfigurations from build time to runtime across your hybrid clouds – AWS, GCP, Azure, OCI, Alibaba Cloud, and VMware vSphere
Learn moreCDR
Continuously monitor your cloud workloads for suspicious activity and collect intelligence from cloud providers to proactively detect and respond to unfolding threats.
Learn moreCNAPP
Wiz is the unified cloud security platform for cloud security and development teams that includes prevention, active detection and response. Use Wiz solution to reduce risk, gain unmatched visibility, accurate prioritization and business agility.
Learn moreEnsure compliance
Maintain automated compliance against industry standard regulations and benchmarks like PCI, GDPR, HIPAA, and more, as well as custom frameworks.
Learn moreIaC scanning
Integrate Wiz into your development workflows to securely manage your infrastructure as code. Detect secrets, vulnerabilities and misconfigurations in your IaC, containers and VM images.
Learn moreVulnerability management
Uncover vulnerabilities across your clouds and workloads (VMs, Serverless, Containers, Appliances) without deploying agents or configuring external scans.
Learn moreContainer & Kubernetes security
Rapidly build containerized applications without risks. Holistically secure containers, Kubernetes, and cloud environments from build-time to real-time.
Learn moreCIEM
Wiz analyzes cloud entitlements and auto-generates least privilege policies across your cloud, to help teams visualize, detect, prioritize, and remediate identity (IAM) risks.
Learn moreContinuously monitor for sensitive data and secrets exposure and proactively eliminate attack paths to prevent data breaches.
Continuously detect and remediate misconfigurations from build time to runtime across your hybrid clouds – AWS, GCP, Azure, OCI, Alibaba Cloud, and VMware vSphere
Unify your workload protection from prevention to real-time detection and response
Continuously monitor your cloud workloads for suspicious activity and collect intelligence from cloud providers to proactively detect and respond to unfolding threats.
Wiz is the unified cloud security platform for cloud security and development teams that includes prevention, active detection and response. Use Wiz solution to reduce risk, gain unmatched visibility, accurate prioritization and business agility.
Maintain automated compliance against industry standard regulations and benchmarks like PCI, GDPR, HIPAA, and more, as well as custom frameworks.
Integrate Wiz into your development workflows to securely manage your infrastructure as code. Detect secrets, vulnerabilities and misconfigurations in your IaC, containers and VM images.
Uncover vulnerabilities across your clouds and workloads (VMs, Serverless, Containers, Appliances) without deploying agents or configuring external scans.
Rapidly build containerized applications without risks. Holistically secure containers, Kubernetes, and cloud environments from build-time to real-time.
Wiz analyzes cloud entitlements and auto-generates least privilege policies across your cloud, to help teams visualize, detect, prioritize, and remediate identity (IAM) risks.
Protecting Your Cloud Environments Requires a Unified, Cloud Native Platform.
Wiz connects to every cloud environment, scans every layer, and covers every aspect of your cloud security - including elements that normally require installing agents. Its comprehensive approach has all of these cloud security solutions built in.
When Wiz says it's
critical — it actually is.
Block your most critical attack paths and protect your sensitive assets
The Wiz Security Graph provides straightforward, context-driven insights into critical exposure.
See what our users think about Wiz
Wiz helps me sleep better at night.

There's a really damn good reason they blast off the edges up-and right on quadrants in their space -- it's not even close out there in practice. From documentation, to UX, to feature deployment, to sales, to support, and beyond, the Wiz team is crushing it every day for us and isn't just one of the best vendors I have today, but have ever had.
Visibility into cloud workloads can be hard, Wiz makes this effortless.

Multi-cloud enablement is at the heart of our transformation strategy and security is paramount. Wiz helps us visualize our entire cloud environment and drive actionable insights, in minutes. They’ve made cloud security an enabler for Morgan Stanley and helped us break down the barriers between security and development teams.

Wiz’s agentless solution was able to get us 100% coverage quickly and at scale. Wiz gives us the contextual view of risks in our environment so we can properly understand and prioritize them based on our knowledge of what’s critical.
Finally a tool that actually gives you the data you need and functional processes.
A "MUST HAVE" Tool in any CISO Stack: Holistic approach, high-quality visibility, reliable and effective. I consider it the most effective tool in my security stack.

Wiz enables us to get more visibility to more teams with more context than we’ve ever had.
Wiz is beyond impressive -- it is a game changer.
Wiz has changed the definition of a fine cloud security tool. I have not seen any cloud security tools capable of doing what wiz does with maximum accuracy. Wiz is straightforward to deploy and presents the findings in a way which makes it really easier for us to focus on severe and critical issues first.

I think Wiz is changing the industry. If you use clouds and you’re scaling, and you don’t have Wiz, you’re in trouble.

I’ve never posted about a product before, but the amount of visibility Wiz can give you with almost no set up is game changing.

Wiz has paid for the five years subscription in a matter of one week.
Wiz is vital in providing the visibility we need across our hybrid cloud environment. We initially put Wiz up against several of its competitors in our selection process, and Wiz made the decision easy for us to choose.
Wiz provides me as a CISO a clear risk-based view of the product lines and divisions I protect. When I advise security leaders of cloud-native / cloud-reliant companies I implore them to explore Wiz, from my perspective this is a required tool in every CISOs toolkit.
Wiz does everything promised and more.

Wiz gives us visibility across our entire cloud stack and provides deeper and broader context on the risks in our environment to prioritize addressing the issues that matter.

Sharing research... 👏 ...results 😍 ...methodology Thank you @wiz_io , you rock!
Wiz is leading the way! Happy customer.
Wiz is allowing our organization to make sense of the highly dynamic and extremely complex multi-cloud environment that is at the base of our infrastructure. Without Wiz, we could never hope to continuously and automatically detect security issues and vulnerabilities as they materialize in our environment.
I am able to prioritize with Wiz with no effort from my part and most importantly I can customize the rules to fit my organization perfectly with unmatched granularity.

We were able to get 100+ findings from Wiz within 2 days of deployment, compared to an individual needing 6 months to deliver that type of information. The time to value and saving at least one headcount is a huge ROI for us.

Amazing job @wiz_io First CosmosDB and now PostgreSQL ! 🔥

ChaosDB vulnerability from @wiz_io team is such an amazing bug, you guys should get more than 100k bounty for this level of severity. Thanks for the clear explanation and the walk through of your researcher mindset. Admirable!!! 👏
New Sheriff in Town: Wiz makes addressing cloud security issues much easier than any other tool I have ever utilized.
I firmly believe that Wiz is worth the hype. The product has given us significantly improved visibility into our cloud security posture - and after only a few conversations/demos, it was clear that Wiz was at least two years ahead of other products in the market (including the native cloud vendor tools!)

Wiz strikes the right balance between providing high-level visibility into our whole cloud posture and giving engineers the hands-on capabilities to resolve issues on the ground. Wiz allows us to scale the cybersecurity team's reach through technology.

Nobody beats the wiz!
One of the best Cloud Security products on the market: Their customer success teams are fantastic and are always very responsive and helpful.
Wiz demonstrates the future of cloud security tools. Wiz avoids the pitfalls of overt complexity, providing a best-in-class security risk management platform that is simple to deploy, easy to navigate and affordable, whilst at the same time providing complete visibility of your cloud technology stack.

Seeing the risks and findings mapped to the different certifications in Wiz really helps me focus and prioritize my work.

The most valued goal for cybersecurity is first frictionless visibility, That one sentence describes Wiz extremely well. Well done Wiz!
Wiz stands on top of the CSPM mountain!

If you have a sizeable cloud presence, you should be considering @wiz_io
In the competitive environment, Wiz has no real competitors. We migrated from first-generation CSPM into wiz with the combined CSPM, CIEM and Vulnerability management and were hugely impressed. The fidelity of the results was a big organizational win and allowed us to prioritize what matters.
Wiz has helped us identify some of the poor practices and approaches we have been taking when using cloud services. Since using wiz, we have been able to address significant concerns, educate our engineering teams on best practices, and take a more secure approach to leverage the cloud for our needs.

What stood out about Wiz for me was it has a very intuitive interface and a really simple dashboard. The fact that it's cloud native and agentless meant we could have it up and running in a matter of minutes and have clear, actionable information
Everyone's time is valuable. Don't let your security posture suffer while trying to sort through a spreadsheet export with 3500 rows. Wiz measures risk along multiple dimensions: vulnerabilities, misconfigurations, clear-text secrets, internet exposure, and available script-kiddie exploits to help you zero in on the most important items to resolve immediately.
After using similar systems and leading tools in the market to protect our cloud, we moved to this tool and we can't stop admiring its endless capabilities. It centers several tools under it in an amazingly easy user-friendly and clear way and one of its great pros is that it's agentless. Excellent and available support and perfect documentation.

Wiz was really the first platform we saw where getting visibility across our entire environment was a one and done set up.

Wiz is the fastest SaaS company to $100M in ARR and $200M in ARR, and has changed how security intelligence is acted upon with a unique data architecture. When you impress Igor Tsyganskiy, you're doing something very right

Sometimes, ignorance is bliss—say, deliberately not checking this week's performance of your retirement account 💸. When it comes to cloud computing ☁️ and protecting Stanford data 🧑🏻💻 however, it can be devastating. You just can't not know. Our team will soon be putting powerful tools ⚡️ with actionable insights 🚨 in the hands of our campus cloud technologists. 🌲
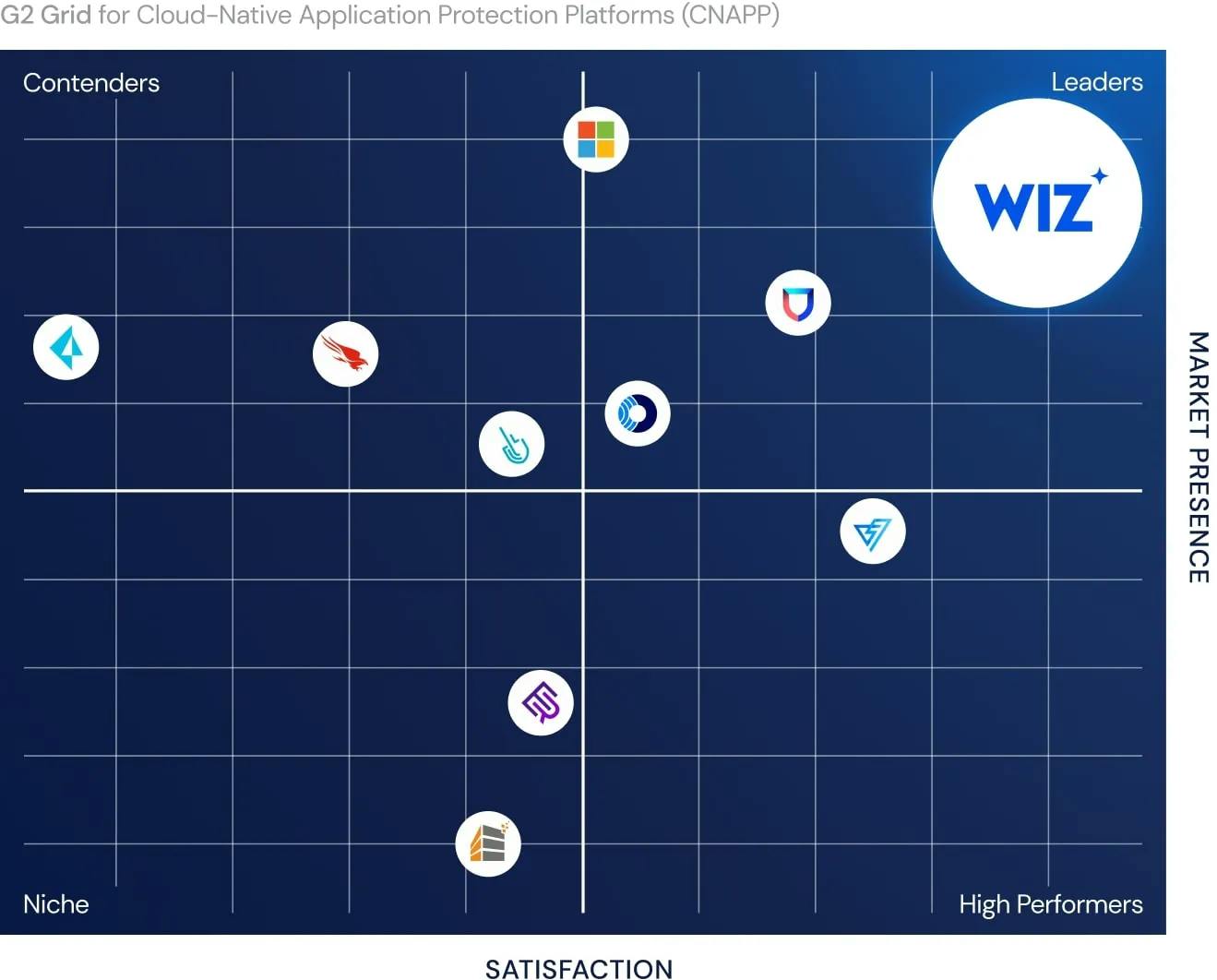
Wiz is the clear leader in CNAPP/CSPM
Don't just take our word for it
“ I have not seen anything else right now that can give you as big of an impact as Wiz. ”
Don't just take our word for it
“ Within a day of deployment, Wiz worked across our entire environment and showed us a set of critical findings that everyone should prioritize immediately. ”
Don't just take our word for it
“ I'm a doctor, I take care of people, I was trained in preventative medicine. Wiz is like preventative medicine for us. ”
Don't just take our word for it
“ This new depth and breadth of visibility really made us pay attention. We were able to scan tenants and find new critical issues very quickly. ”
Yes, Wiz integrates
with
Wiz Integration (WIN) platform enables bi-directional sharing of security findings across the cloud security ecosystem to reduce risk, improve efficiency and enable an open cloud security ecosystem.
See our 60+ integrationsLatest Research and Publications
Ready to see Wiz in action?
“Best User Experience I have ever seen, provides full visibility to cloud workloads.”
“Wiz provides a single pane of glass to see what is going on in our cloud environments.”
“We know that if Wiz identifies something as critical, it actually is.”